Save time with Just-In-Time User Provisioning


Some of the best features are the invisible ones, that you don't know you need until you don't have them. That is why our team at GoodData has been working on Just-In-Time (JIT) User Provisioning.
Currently, every time our client wants to add a new user to their organisation, their admin has to create the user in their OIDC provider, then create a corresponding user in the GoodData Platform ( and map one to the other correctly). Then he has to assign this user to the desired user groups, etc.. You get the idea: It's a lot of manual work.
That is why, we're introducing the JIT provisioning, where the client will only need to define the user in their OIDC provider, and we will handle the rest. Essentially adding users on demand the moment they want to access our analytics, making it seamless to add more people for collaboration or adding another stakeholder.
Important aspect of this change is that there are not many changes required on the side of the customer's OIDC provider.
How does it work?
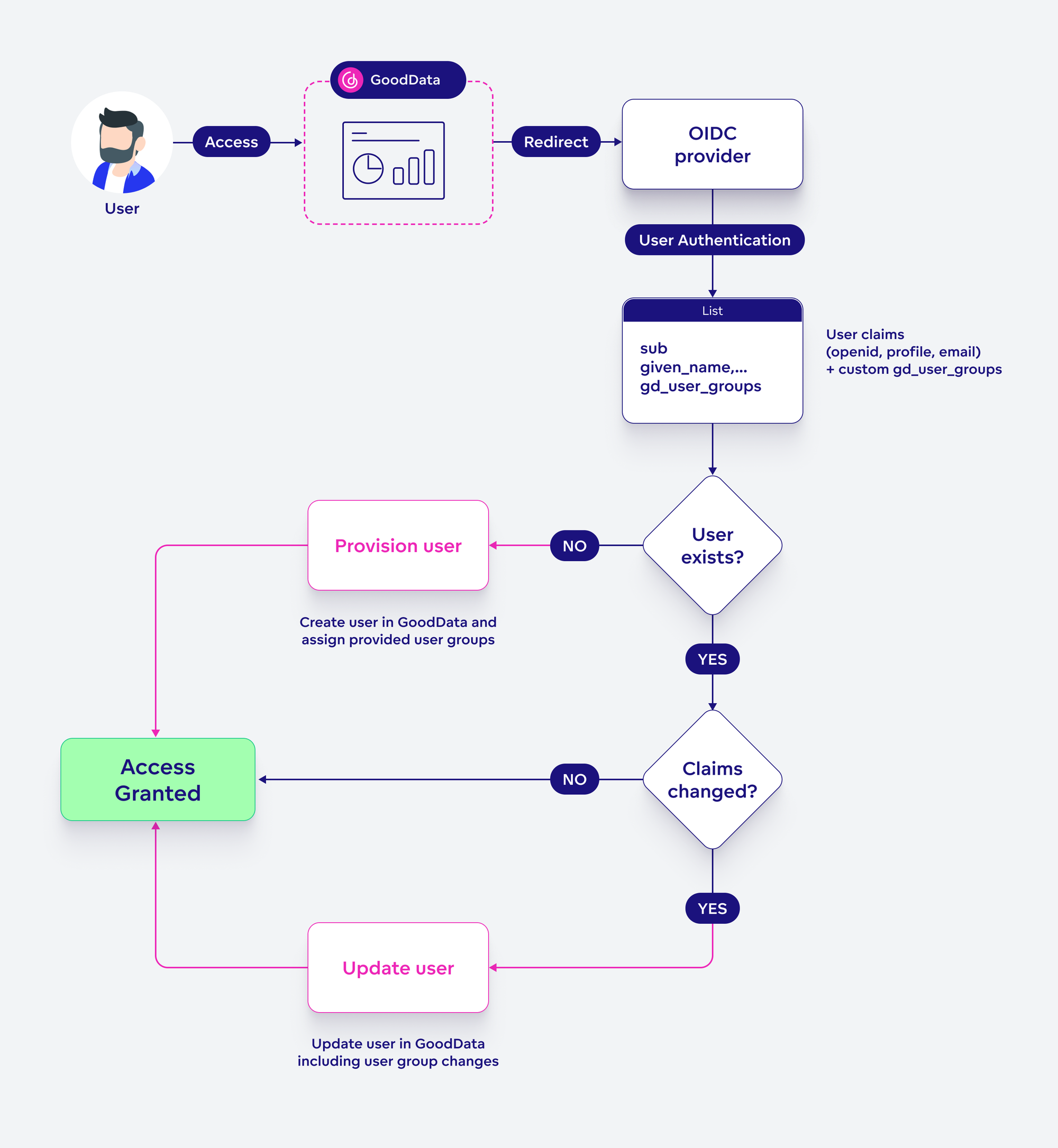
For it to work, we need to enable the JIT provisioning for the particular customer (done on our side) and then the customer makes sure that the OIDC provider is sending all the necessary claims (login request fields).
Configure authentication provider to send id token with the following claims:
- sub
- given_name, family_name
- urn.gooddata.user_groups(optional custom GoodData claim containing list of users userGroups)
Since we have no additional info about the newly created users (at the time of creation), we highly recommend you add the user group(s) to the claims, to ensure the appropriate access to workspaces, as you might not want to give everyone admin.
You can also use the claims to update existing users. Once the claims contain given/family name, email or user groups fields, those values are propagated to the GoodData platform.
To make it even easier, you don't need to provide an existing user group in the claims. If it does not exist, a new empty group is created.
So to see the whole story, this is what the JIT user provisioning adds two branches to the basic User Authentication.
And that’s it for now. Would you like to learn more about JIT? Let us know at our Community Slack and we will create a walkthrough for you! :)
Want to learn more?
Here are a few relevant documentation pages, like how to Set Up Authentication using OIDC Provider, the OIDC Authorization Code Flow, Authentication in GoodData Cloud and how to Manage Organization.
Want to try it yourself? You can use our Free Trial!
If you would like to see what else we are working on at GoodData, check out our GoodData Labs!


