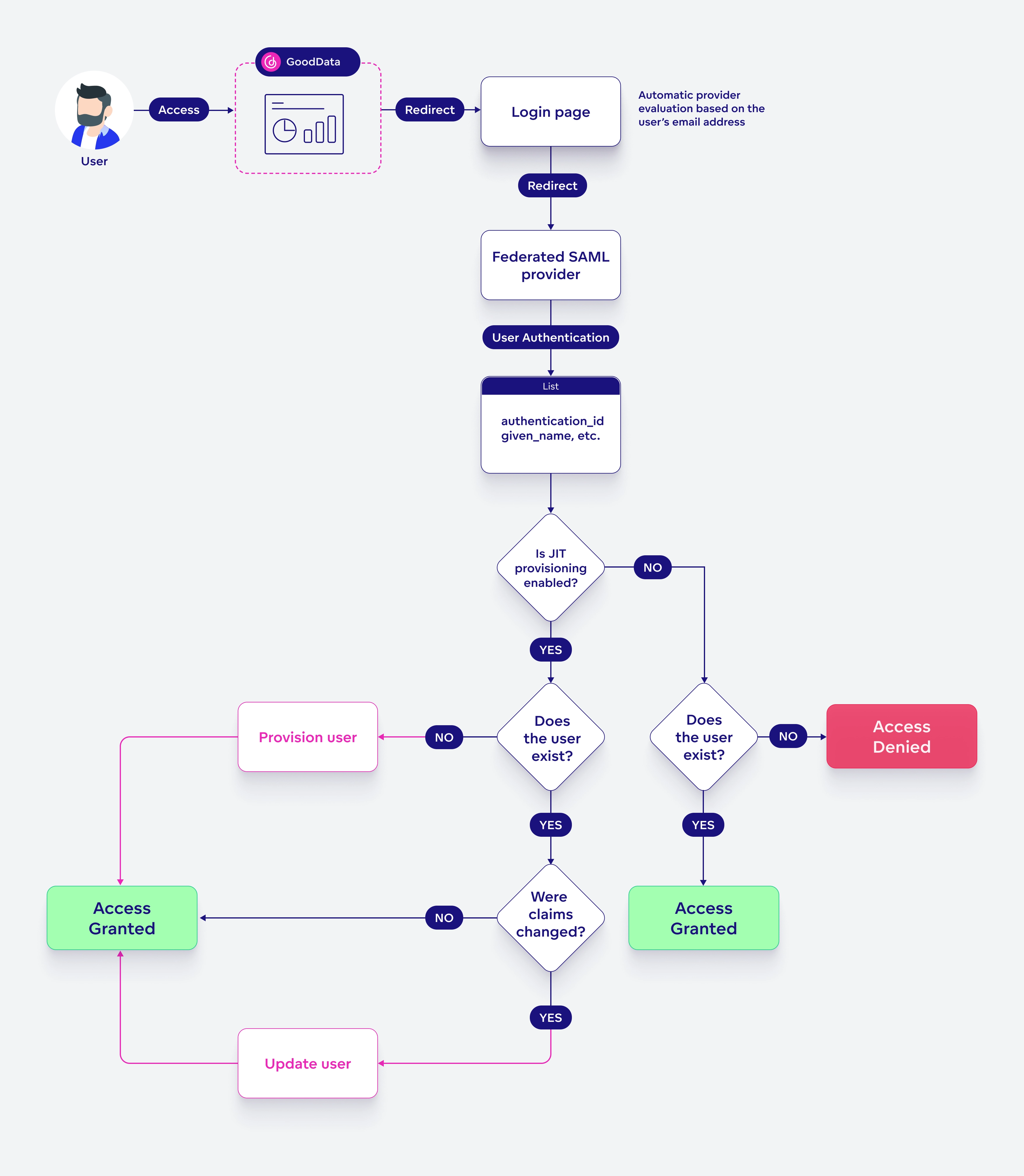
SAML Authentication
The SAML authentication logic is nearly identical to MOIDC authentication.
To set it up, follow the MOIDC setup guide and change the details described below.
Note
The Federated Identity Management feature, which includes using multiple OIDC providers and SAML authentication, is available only as part of the Enterprise tier.
SAML Configuration
SAML configuration uses the same API endpoint as MOIDC but with a slightly different payload. Instead of OAuth-related parameters, it uses the samlMetadata parameter, which should be defined by a Base64-encoded XML document containing the SAML metadata.
Example: Registering a SAML Provider
To register a new SAML provider, send a POST request to the /api/v1/entities/identityProviders API endpoint with the following payload:
{
"data": {
"attributes": {
"customClaimMapping": {
"property1": "string",
"property2": "string"
},
"identifiers": [
"gooddata.com"
],
"idpType": "CUSTOM_IDP",
"samlMetadata": "string"
},
"id": "id1",
"type": "identityProvider"
}
}Parameter Notes:
samlMetadata: Contains the full metadata XML for the SAML provider, base64 encoded to a string. The content is limited to 15,000 characters.identifiers: A list of domains or entity identifiers associated with the identity provider (e.g.,"gooddata.com"). See the Setting Up Multiple OIDCs section for details.customClaimMapping: Used to map SAML assertions to internal attributes. See the Custom Claim Mapping section for details.
Custom Claim Mapping
When configuring an Identity Provider (IdP) — whether OIDC or SAML — in Amazon Cognito, it is necessary to specify which user attributes the IdP supports and returns in its authentication response.
For example:
- If the token comes from IdP A, it might include attributes like
name,familyName,givenName,email, etc. - If it comes from IdP B, the token might use attribute names like
family_name,given_name,email, and so on.
To handle this variation, Cognito uses attribute mapping, which defines how IdP-provided attributes map to Cognito’s internal user profile attributes. In the Cognito UI, this mapping is visualized in an Attribute Mapping table with Cognito attributes on the left, and Token (IdP) attributes on the right.
For OIDC providers, this is typically straightforward because they usually follow standard naming conventions (sub, email, family_name, given_name, name), allowing the default mapping to work out of the box.
However, SAML providers often use custom or non-standard attribute names. Therefore, custom claim mapping is essential. You must define explicitly how the SAML token attributes should map to Cognito attributes when setting up a SAML IdP.
Example of a required customClaimMapping for a SAML IdP:
"customClaimMapping": {
"sub": "NameId",
"email": "Email",
"given_name": "Fname",
"family_name": "Lname",
"name": "Name"
}Without this mapping, Cognito won’t be able to correctly interpret the incoming attributes from the SAML token.
Limitations
SAML supports Just-In-Time (JIT) provisioning, but with certain limitations. Currently, only the following use cases are supported:
- Basic JIT provisioning – Automatically creates a user when they first sign in.
- JIT provisioning with predefined user groups – Automatically assigns users to predefined groups during provisioning.